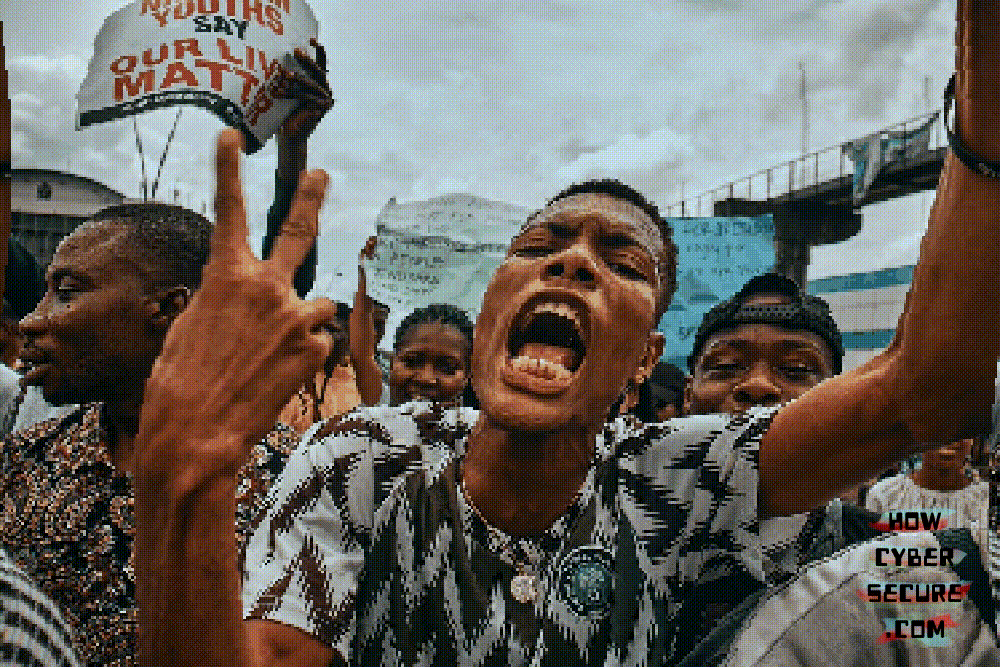Arizona Senate Must Disclose Who is Funding Its Election Review Program (Election Review)
by Team

Computer Security – The Arizona Supreme Court on Monday ruled that Arizona Senate must disclose who is funding it’s election review program (election review). The ruling means that the state Senate must make the name of the outside companies who are funding it’s election review program public. The ruling comes at a time where the state is trying to decide if it should continue to fund its election review program. The state began the search for the new state senators in January after redistricting.
The case involves a $200 million lawsuit initiated by the state in April 2014. In that lawsuit, the state argued that it was the legal requirement of state election law to disclose who is funding its review of each legislative bill. It argued that the Senate had not previously been required to be transparent about who is funding its election review program and that its continued funding was a violation of the state constitution if any of the companies funding it were state employees. In July 2014, the Arizona Supreme Court agreed with the state and ruled that the state Senate had to make the outside entities funding the program publicly known on the Senate’s website.
The ruling means that the state Senate must make the names of all companies funding it’s election review program public on the Senate’s website. The ruling comes at a time where the state is trying to decide if it should continue to fund its election review program. The state began the search for the new state senators in January after redistricting.
The case involves a $200 million lawsuit initiated by the state in April 2014. In that lawsuit, the state argued that it was the legal requirement of state election law to disclose who is funding its review of each legislative bill. It argued that the Senate had not previously been required to be transparent about who is funding its election review program and that its continued funding was a violation of the state constitution if any of the companies funding it were state employees.
The resubpoenaing of the 2020 Audit Maricopa County.
Article Title: The resubpoenaing of the 2020 Audit Maricopa County | Computer Security.
“Audit of Maricopa County. ” This is the title of two of the 2020 audit reports by the County of Maricopa. The first report of the auditors has been completed and submitted to the Department of Management Services, the next is not completed until May.
The county received its initial audit in 2018. The two reports were presented to the Maricopa County Board of Supervisors on February 15, 2019. The three-page reports included the information for the 2018 tax year and 2019 tax year.
The two reports on the 2018 tax year provide important information on the results of Maricopa County’s audit. The counties auditors looked at the County’s audit file on Maricopa County, but did not have access to the files of the other three counties. The audit reports showed that the County tax records show an increase in both county and city taxes, but that county revenue is lower than expected.
The audit report on the 2019 tax year showed that the County increased county tax revenue in the initial year to $13,068,651, which amounts to $1,072,812 per capita. From the second year onwards, the county has shown an increase in county tax revenue to $15,947,632, which amounts to an increase of $9,292,819 per capita.
The audit report on the 2018 audit indicates that the current value of county property taxes is a little higher than the tax value at time of audit in December 2018 and December 2019.
The audit report on the 2019 audit was presented to the board on March 20, 2019. The report included the information for 2018 tax year and 2019 tax year. (In the 2018 audit, the county auditor reported that a tax lien had been filed against the property of the Maricopa County Supervisor’s Office. The county auditor’s report notes that the tax lien occurred in the amount of $18,500,000.
The report on the 2019 audit covers about a six-month period from January, 2018, to January, 2019.
Morning News –
Computer security has changed dramatically in the last decade. One of the main changes is the emergence of the Internet and the evolution of the Internet. We no longer need dedicated servers and dedicated hosting for our clients. We now have our own dedicated servers online. With online hosting, we can host as many servers as we need for our business. We can move servers around online and move from one server to another server with ease. We no longer need dedicated servers. The Internet has made it easy to host any number of servers in the same physical location. We need only a web site hosting to connect our servers to the Internet.
The evolution of the internet has increased the number of security threats. The number of threats increases as the Internet expands and the Internet becomes more complex. If we think about the number of security threats, we can see how complex the Internet is. It has become more and more complex, so that you should consider how to secure the Internet.
The Internet is a huge collection of interconnected computer networks that are constantly being exploited by numerous security threats. There is nothing that can withstand what the Internet can provide. However, there are methods to make the Internet less vulnerable. The good that the Internet can provide to us is increasing the security of the Internet and increasing our safety.
There are many methods to secure the Internet. Some methods are more secure than others. One of the methods that have become more popular in the last decade is the use of encryption technology on the Internet. Encryption is a way to protect the communication between computers. It is the process of providing a way for a computer to send its data in a secure way. This is one method that improves the Internet’s security. It is important to note that the encryption method used on the Internet should not be regarded as fool proof. It cannot be considered as 100 percent secure. Some security products can be easily cracked. However, cryptography is not foolproof. It always has the possibility of being cracked.
There will always be a way that a hacker can break through the encryption. We can make the hackers stronger. We do need good encryption software to protect our computer systems from hackers. However, sometimes, encryption software can be used incorrectly. We need to understand that encryption software is not fool proof.
Rejected to comments on Sharpies in Maricopa County’.
Article Title: Rejected to comments on Sharpies in Maricopa County’ | Computer Security.
Reprinted from Security Affairs. Reprinted with the permission of Security Affairs.
The Arizona State Library and Archives, in conjunction with the University of Arizona, has a number of items related to computer security and computer history in its special collections. Among these are some handwritten notes by Steve Bittel, a computer programmer and entrepreneur who helped to popularize the concept of a computer virus and the term “bug”. Bittel was a graduate of the University of Minnesota, and is now known to some as the “father of the virus”, though of the time he was working on his Ph. thesis, it is known he first created the idea of a virus while he was still in his late twenties.
Many of the Bittel notes were donated by Bittel’s wife and their daughters, and the archive hopes to locate them for their families. Included in the collection are several typed pages from a 1990 article in a computer magazine of the then current status of computer security, including the term “sinkhole”.
In addition to the archive itself, the University of Arizona has a collection of several dozen computer magazines called the Bittel Archives from the early 1980s through the early 1990s. The collection includes a variety of computer magazines such as PC World, PC Magazine, PC Magazine Online, and Popular Science.
The Bittel Archives provide the University of Arizona with an excellent opportunity to investigate how technology has affected the way we have interacted with the world and the way our lives have developed over the past 80 years. It is hoped that the archive will offer the reader a more complete understanding of the ways in which the computer has changed the world.
Tips of the Day in Computer Security
OpenSSL is an open-source software that is popular among people who are interested in cryptographic technology and security. This software was designed by the software company Boring Company LLC and has many users around the world. If you are a developer then you probably use this software and are also interested in security and cryptography.
OpenSSL is one of the most important tools to build the cryptography technology in your computer and secure your data. The code of OpenSSL software is released under the BSD license so you can freely use this software if you are interested in cryptology but not in security.
In addition to the cryptography, another purpose of this software is security because the code of OpenSSL has no bugs or security vulnerabilities.
On the other hand, the code is not free so you should be careful with it.
Related Posts:
Spread the loveComputer Security – The Arizona Supreme Court on Monday ruled that Arizona Senate must disclose who is funding it’s election review program (election review). The ruling means that the state Senate must make the name of the outside companies who are funding it’s election review program public. The ruling comes at a time…
Recent Posts
- CyberNative.AI: The Future of AI Social Networking and Cybersecurity
- CyberNative.AI: The Future of Social Networking is Here!
- The Future of Cyber Security: A Reaction to CyberNative.AI’s Insightful Article
- Grave dancing on the cryptocurrency market. (See? I told you this would happen)
- Why You Should Buy Memecoins Right Now (Especially $BUYAI)