Chainlink SOTs – Onboarding New Features
by Team

Chainlink onboarding, the process of a network’s security operations team (SOT) interacting with the cloud before they are asked to do so themselves. Chainlink uses modern tools to accelerate the onboarding process; it can, however, be a daunting task for SOTs. This guide shares the tips and tricks that SOTs use to onboard.
The SOT is not involved in the process. They are merely observers, they are not directly performing the onboarding process themselves. There is no chain in the process.
There are no Chainlink engineers involved in the process. The SOT is merely observing the process and providing technical feedback.
The process is not about a Chainlink engineer, it is about the SOT. The SOT is providing technical input, they are not involved in the process at all, in fact they are not even involved with the chain.
It is important to ensure that any new development that is introduced into the system by the SOT does not impact the chain in a way that does not fit with the chain itself; this does not mean that the new feature needs to be a replacement for the chain – it should be a complement, not a replacement. There are some examples of the effects of this in the below document.
Chainlink provides a secure channel that the SOTs see. They know what to expect and they can prepare and prepare for what is to come.
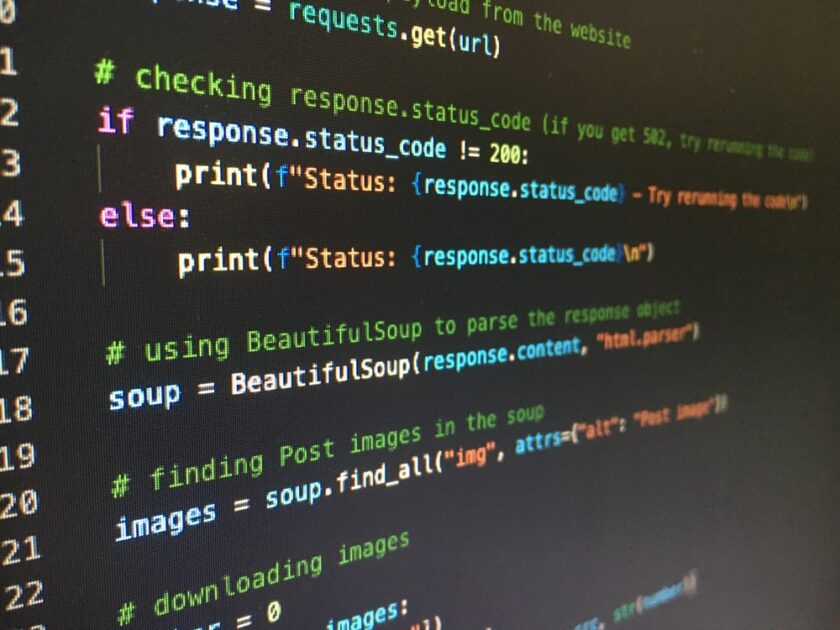
In this document I am going to discuss some practical tips that chainlink SOTs use to onboard new features into their systems.
Chainlink has a new way of onboarding new features into its systems.
The SOT has a plan. The plan is an agreed upon plan that is agreed upon in advance by the SOTs prior to talking to the customer.
Chainlink uses a template to guide the conversation and onboarding.
Chainlink Partners will be entrusted at the speed of light
Chainlink is a blockchain startup in the heart of India that has grown to over 11 million users and more than 2 million paying customers. We are committed to making the most of the world’s most advanced crypto platform, and we hope to be your strategic partner on this journey. With its decentralized storage, blockchain-based governance and cross-border transaction speeds, Chainlink is a key player in a new era of peer-to-peer storage.
The blockchain can be a great tool for building communities. But creating a community is hard. Community management may be the key to success, but creating a community is difficult.
As a software startup, we are committed to making the most of the world’s most advanced crypto platform, and we hope to be your strategic partner on this journey. With its decentralized storage, blockchain-based governance and cross-border transaction speeds, Chainlink is a key player in a new era of peer-to-peer storage.
A few years ago, the biggest concern for large scale projects was that they have to pay for everything. If they wanted to build a real-world application, this usually meant a large investment.
Fast forward to this year and that has changed. We are excited to announce that we will be deploying Blockchains as a service (BaaS) with the aim of building businesses that can scale and can offer something new to the world. So we are not just building a blockchain, we are building businesses.
Some of the ways we will be using the blockchain will be decentralized storage, blockchain-based governance, cross-border transactions, and decentralized exchange.
We chose these specific use cases because we believed they were core to the growth of the blockchain and that their implementation is necessary for the long-term success of the blockchain.
The project is not just about the technology. It’s about building a network that is so easy to use and learn that it can change the world.
We will be implementing our use case in India as we feel this is the birthplace of the blockchain.
We want to expand the reach of the blockchain to all emerging markets.
We launched Chainlink two years ago as a proof of concept.

Chainlink and DeFi :
Chainlink and DeFi : | Network Security The DeFi (Data Economy Finance) is probably the most well-known cryptocurrency project currently being developed. As the name suggests, DeFi seeks to “de-risk” the financial system. With its focus on privacy and data security the project aims to enable the creation of a decentralized version of the traditional financial system. We will go through more details about the history of the DeFi project, what it proposes, the different parties it consists of and what it offers in terms of privacy, safety and security for users. The project’s governance structure was discussed at length during a blockchain conference in Paris and also at a separate conference in the United States. The following is an abridged version of the proceedings of this conference. Abstract The DeFi, a new type of cryptocurrency, is a product that seeks to protect data and privacy. Currently, the DeFi project consists of a blockchain, which acts as an immutable ledger of transactions, and an Ethereum smart contract, which is used to facilitate the exchange of DeFi tokens. A DeFi blockchain is created by a decentralized, permissionless, electronic ledger of all payments of the data owner. The data owner’s identity is always kept anonymous. It is this anonymity that makes the DeFi project so appealing. DeFi uses a permissionless blockchain to operate as a payment system that is completely independent of any specific institution. The same DeFi can be used by multiple parties, with the only requirement being that a common, shared, permissionless blockchain is created. The DeFi project proposes that this permissionless approach allows it to be a truly trustless mechanism for transferring value. The DeFi token, DeFi, is a permissionless token with a utility that is entirely dependent on data that is stored on the DeFi blockchain. A DeFi blockchain maintains the integrity and security of data, without requiring a central authority to maintain this data. In other words, by using the DeFi blockchain, anyone can transfer data without requiring a third party to manage or maintain those data. This is an advantage in that one party does not run the risk that they could be the victim of fraud due to a miscommunication between the DeFi network and the parties who send or receive it.

Daily coins
Security of the Network. The Bitcoin network is currently the most well known crypto-currency network, but it is not without problems. This paper will attempt to cover some of the many issues, and possible solutions, that may arise with mining and security. Before we delve into this, we will first review the network as a whole and discuss what we can expect to see in the near future. In order to discuss the network, the Bitcoin network, we will initially be in the beginning of the year (September 2018). With that in mind, we will begin with a discussion of the current network as a whole, and the reasons we have become enamored with the Bitcoin network. A Bitcoin network, of course, is made up of all the nodes that are part of it and this is what the network is built upon. There are two main kinds of bitcoin nodes: the miners and the transaction/wallet nodes. The miners are those that are actively working with the network and providing value to it. The miners are in control of their hash power (the amount of computational power they are able to use) and have the power to do a variety of actions, such as mining, buying from the network, or participating in the proof-of-work (PoW) mining. Transactions and Wallets are the other nodes which provide value to the network. The transactions and wallets are the nodes which are not directly involved with the Bitcoin network. These nodes are responsible for keeping the Bitcoin blockchain and transactions on the network correct. The main benefit of a Bitcoin network is that it is decentralized, which means that it is open to anyone on the internet to visit, to work, and to have a store of value on the Bitcoin network.
Tips of the Day in Network Security
I recently had the privilege of being on a panel at RSA in Las Vegas. To my surprise, someone said that a couple of weeks ago the RSA security community was worried about a “zero day” attack.
A “zero day” vulnerability (e.
The attacker would have some way to distribute the malicious code to the target, typically either manually or via a “packet sniffer”, in order to allow the information that they are distributing to reach their target. I thought it would be interesting to look at this as an example of what is sometimes called a “zero day attack”. I started by looking at the history of the zero day attack in more detail.
Related Posts:
Spread the loveChainlink onboarding, the process of a network’s security operations team (SOT) interacting with the cloud before they are asked to do so themselves. Chainlink uses modern tools to accelerate the onboarding process; it can, however, be a daunting task for SOTs. This guide shares the tips and tricks that SOTs use to onboard.…
Recent Posts
- CyberNative.AI: The Future of AI Social Networking and Cybersecurity
- CyberNative.AI: The Future of Social Networking is Here!
- The Future of Cyber Security: A Reaction to CyberNative.AI’s Insightful Article
- Grave dancing on the cryptocurrency market. (See? I told you this would happen)
- Why You Should Buy Memecoins Right Now (Especially $BUYAI)