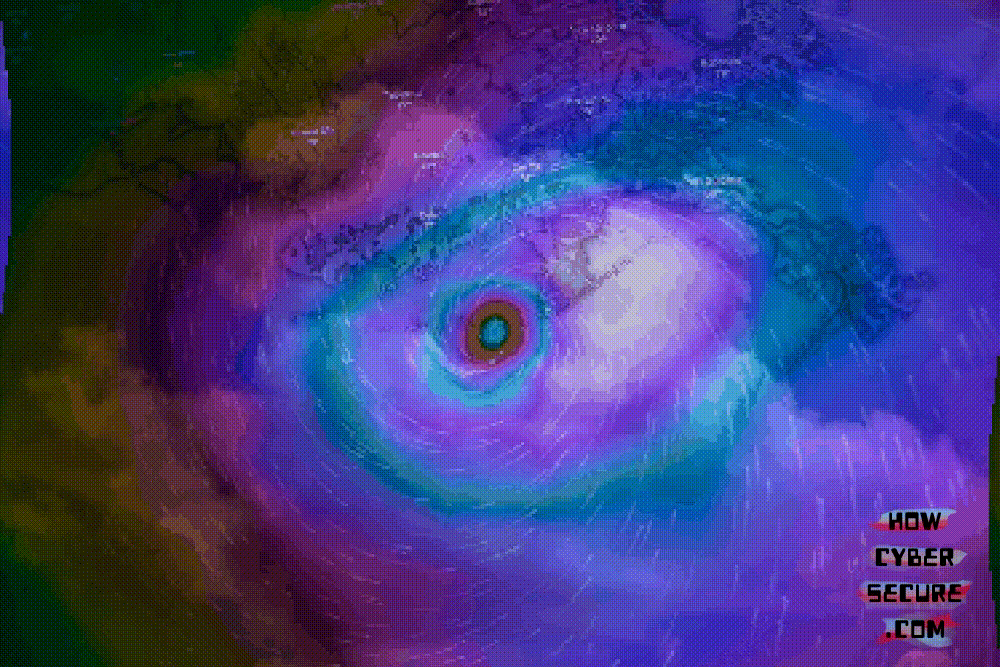
Ida Strengthens to a Category 2 Storm
by Team

Ida Strengthens to a Category 2 Storm — Computer Security — A Category 1 Storm in the Atlantic is in sight, and the hurricane that is forecast to arrive in the next two or three days is a Category 2 storm.
I was born in New Hampshire, where I was raised, and lived in Florida until I was 6 or 7 years old, when my family and I moved to the mountains.
It seems to me that life is just going by now. Life goes by fast. And you want to make it go faster.
To make life go faster, I do a lot of thinking about things before I move or when I make a decision, so that I’m fully prepared for an event.
In these times of uncertainty, there are only so many choices.
Here are some examples.
The New Hampshire-Florida Migration. I was born in Northport, New Hampshire, and have lived in Florida since my birth, when my father moved there to work on a farm. He and I moved to New Hampshire together. I’m still friends with about fifteen of my friends and family and they have remained in touch with me. My sister lives in Jacksonville, Florida, where she was born and educated. My brother lives in New York City. My parents still live in New Hampshire, and we all see each other from time to time. Our friends in our families live in New Jersey, Ohio, and New York City. My in-laws live in South Florida. Of course there are many others.
I grew up in a small-town community in upstate New Hampshire. We were close with our church neighbors, our church friends, our town friends. But I still spend a lot of time outdoors with my family, fishing, hunting, camping, and outdoor activities. Hunting, fishing, and camping are very important to me.
The hurricane that I am describing is much worse than anything I have ever experienced before. It’s one of the most destructive storms known to man.
Michael Richard from Creole Cuisine Restaurant Concepts in the French Quarter before the fall of Hurricane Ida in New Orleans.
On March 11, 2001, approximately 10 minutes after the first of the two Hurricane Katrina hurricanes arrived in the Mississippi and Alabama coastal areas, the most powerful hurricane ever recorded in the United States, the second hurricane to strike the northeastern United States, the most powerful tropical cyclone to hit the United States in the twentieth century, the fifth hurricane to make landfall in the United States since 1900, the first hurricane to hit the Mississippi and Alabama coastlines since 1895 and the first hurricane to hit the Mississippi and Alabama coastlines since 1900, the first tornado to make landfall in the United States since 1900, the second tornado to make landfall in the United States since 1900, the fifth tornado to make landfall in the United States since 1900, the first tornado to hit the Mississippi and Alabama coastlines since 1900, the third tornado to make landfall in New Orleans since 1900, the second tornado to make landfall in New Orleans since 1900, the second and third tornadoes to make landfall in New Orleans since 1900 and the first and second tornadoes to make landfall in New Orleans since 1900, Michael Richard from Creole Cuisine Restaurant Concepts in the French Quarter before the fall of Hurricane Ida in New Orleans, Louisiana, was killed by severe and life-threatening injuries he sustained when a house he was renting exploded in a severe tornado outside of his mobile home in the French Quarter. Michael Richard, an African-American, was born March 3, 1965, in the city of Los Angeles. He had arrived in New Orleans on March 15, 1979, by helicopter to serve as a cook at Creole Cuisine Restaurant Concepts located in the French Quarter before the fall of Hurricane Ida in New Orleans, Louisiana.
On the day of the storm at approximately 9:30 a. , Michael Richard, wearing blue jeans and a brown jacket over the top, was working at the cafe serving lunch in the French Quarter when he was crushed to death by an EF5 tornado on the ground on the East Bank of the Mississippi, which struck Michael Richard’s home at 3911 Grosvenor Avenue, located in Carrollton, Louisiana.

Ida, the greatest catastrophe in the city!
Ida, the greatest catastrophe in the city! : Computer Security.
By Thomas C.
Ruhrpammerwerk, the Ruhrpammerwerk Factory, in 1933.
the buildings in the city center, and which is now being repaired.
later, was the collapse of the Ruhrpammerwerk.
building construction methods.
was made public.
construction of new buildings.
catastrophe.
application of the new-type machine-made building construction method.
method of a particular system.

The night was Ida, a Category 2 hurricane, arriving late.
| PDF: Introduction to Computation Security 1 Introduction Many authors are aware of the importance of computer security. In the 1990s, the first vulnerability in a widely used system was discovered and reported to the manufacturer. This led to the industry working toward a better defense in the face of such an attack. In this chapter, we will look into ways to improve security. In particular, we will look at how to attack modern day computing systems and how to defend against such attacks. This chapter offers a general overview of how to protect systems today, and not only the more traditional attacks such as malware, worms, and Trojans. In addition, we will also look into how to improve the security of a system. Finally, we will examine the differences between traditional security techniques and modern attack techniques. 2 Computer systems fall into many categories, including servers, desktops, laptops, netbooks, and phones. These systems are often used for different activities. Typically, each of these systems are connected to the Internet, and many of these will be used for internet-connected applications. The attacks which we will look into focus on a specific category, such as computer networks, security vulnerabilities, or file systems. In this case, a system is being attacked to perform a specific function or function a specific way. For example, an attacker would want to perform a certain operation on a file that does not normally access files. This attack would use a type of attack which is usually known as a denial of service attack, or DDoS attack. We will also look at how to protect systems from hacking, but in a very different way. 3 Our objective is to provide you with an overview of how to improve computer security as a whole. In this chapter we will look at techniques for improving security and defense, and how some are more effective than others. 4 This chapter focuses on the basic principles of computer security, and does not provide details on how to create the security techniques. However, it does contain an overview of a few attacks that can be used to improve security. We will provide additional details on specific techniques in several chapters of this book. This is one of the most important things to keep in mind when reading this chapter. We do not want to get too technical for our readers. Therefore, we provide step-by-step guides.
Tips of the Day in Computer Security
This is an archived article and the information in the article may be outdated. Please look at the time stamp on the story to see when it was last updated.
HELPDEAC: A massive security breach of company files has been brought to light, reports Computerworld. The breach occurred in 2010, when a database containing credit card data was stolen from a company in Australia.
The records of the breach have been made secure after the theft, but the extent of the breach is still being examined. Some customers have used the credit card data for fraudulent purchases, but at times, the stolen data was not used in transactions, and the customer may not be aware of any fraudulent activity.
The breach was discovered by hackers, and the FBI is investigating the matter. For many people, the breach has caused a lot of anxiety because they now need to remember hundreds of credit card numbers, which were previously removed from circulation. These numbers include the customer’s name, address, date of birth, name and address of the issuer, and other information.
Related Posts:
Spread the loveIda Strengthens to a Category 2 Storm — Computer Security — A Category 1 Storm in the Atlantic is in sight, and the hurricane that is forecast to arrive in the next two or three days is a Category 2 storm. I was born in New Hampshire, where I was raised, and lived…
Recent Posts
- CyberNative.AI: The Future of AI Social Networking and Cybersecurity
- CyberNative.AI: The Future of Social Networking is Here!
- The Future of Cyber Security: A Reaction to CyberNative.AI’s Insightful Article
- Grave dancing on the cryptocurrency market. (See? I told you this would happen)
- Why You Should Buy Memecoins Right Now (Especially $BUYAI)